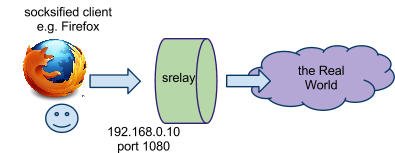

configuration in /etc/srelay.conf:
# dest dest-port
0.0.0.0 any
command line for starting-up
$ srelay -c /etc/srelay.conf
Note:
above example is default configuration. so, you may get same effect as
$ srelay
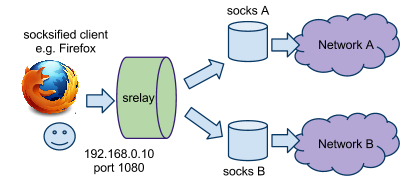
configuration in /etc/srelay.conf:
# dest dest-port next-hop next-port
Network_A any socks_A 1080
Network_B any socks_B 1080
Note:
Network_A, Network_B may be actual network addresses.
socks_A, socks_B are host addresses and their ports may vary on configs.
you may guess that you can also add
0.0.0.0 any
at the end of the srelay.conf for networks other than Network A and B.
srelay.conf's lines are evaluated as line order.
Note(2):
DESTINATIONS
Destinations are some of IPv4, IPv6, and FQDN. If your SOCKS client requests
“REMOTE” Resolve, that request may have destination as FQDN.
If you would like to control that kind of destination, you have to set FQDN
destination in a config line. In many cases, a FQDN might be useless, so, you can
do something using wildcards as destinations. Sub-domain match of FQDN is in
my ToDo.
Wildcard DESTINATION
IPv4 0.0.0.0
IPv6 ::
FQDN *
Example
# dest dest-port next-hop next-port
0.0.0.0 any 10.0.0.1 1080
* any 10.0.0.1 1080
Meaning that every (IPv4, FQDN) destination should go through the next
Hop SOCKS of 10.0.0.1 port 1080.
As of srelay-0.4.8b6, FQDN destination “*” in config line will match not only FQDN
but, IPv4 or IPv6. So, be careful using the newer releases.
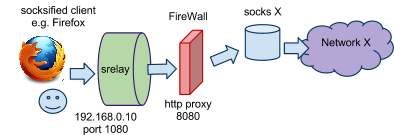
configuration in /etc/srelay.conf:
# dest dest-port next-hop next-port nnext-hop nnext-port
Network_X any socks_X 1080 FireWall 8080/h
Note:
Destination and relay hosts are placed farthest first order in a config line.
In this case, we assume that FireWall has http proxy which supports
HTTP CONNECT method proxy and offers no proxy-authentication.
The port number followed by '/h' means that host speaks HTTP PROXY.
The port number followed by nothing or followed by '/s' means SOCKS
proxy as you can guess.
currently, this function has not been tested well and very limited support
against HTTP Proxy specs.